Earlier this month a new ransomware operation began performing targeted attacks against numerous companies with customized attacks that have already earned them million-dollar payouts.
In a press release that was shared by the threat actors, they claimed to be former affiliates of other ransomware operations that have made millions of dollars. After not being able to find a product that suited their needs, they decided to launch their own operation.
They say, they only target companies that can pay the specified ransom and they go on to add that they only target companies that can pay the specified ransom.
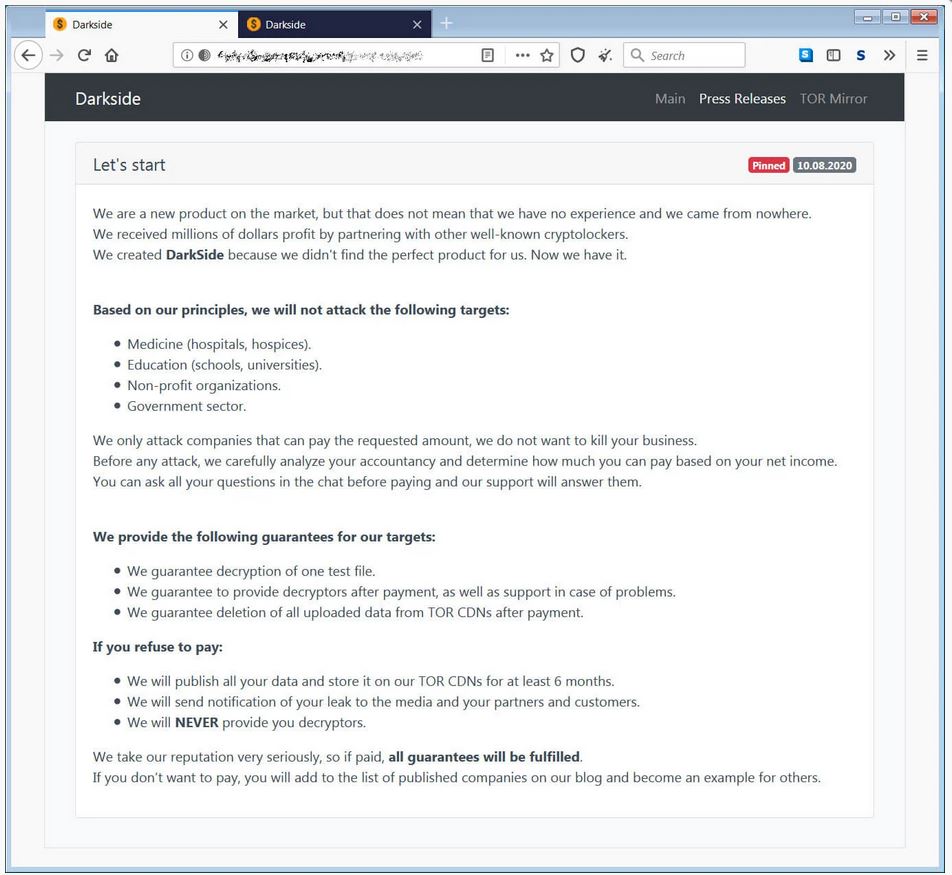
They have also stated that organizations operating in the following sectors won’t be targeted –
- Healthcare
- Education
- Non-Profit Organizations
- Government Sector
However, only time shall tell if they honor their statements.
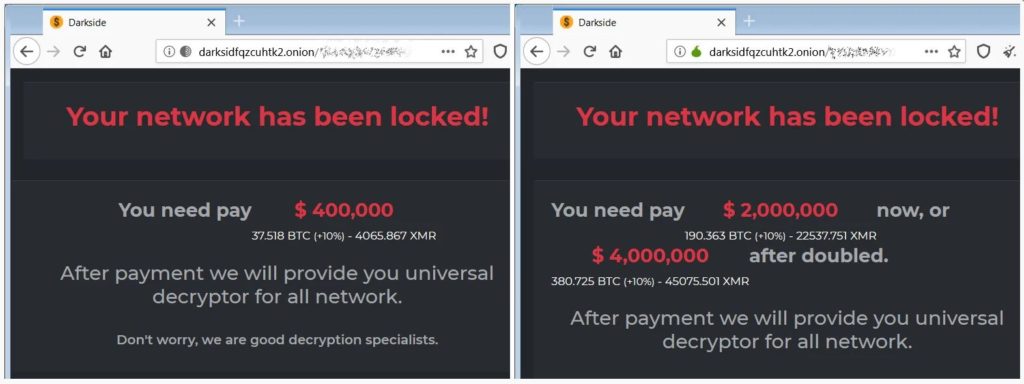
According to researchers, DarkSide’s ransom demands range from $200,000 to $2,000,000. However, these numbers could vary depending upon the victim. It is reported that at least one of the victims has paid more than a million dollars in Ransom.
Like other ransomware attacks executed by various threat actors, when the network is breached by Darkside threat actors, they will spread laterally throughout a network until they gain access to an administrator account and the Windows domain controller. The attackers will then harvest unencrypted data from the victim’s servers and upload it to their own devices, while they spread laterally.
The data that is stolen is then posted to a data leak site under their control and used as part of the extortion attempt. Post this step, the threat actors will share information like company name, the date they were breached, how much data was stolen, screenshots of the data, and the types of stolen data.
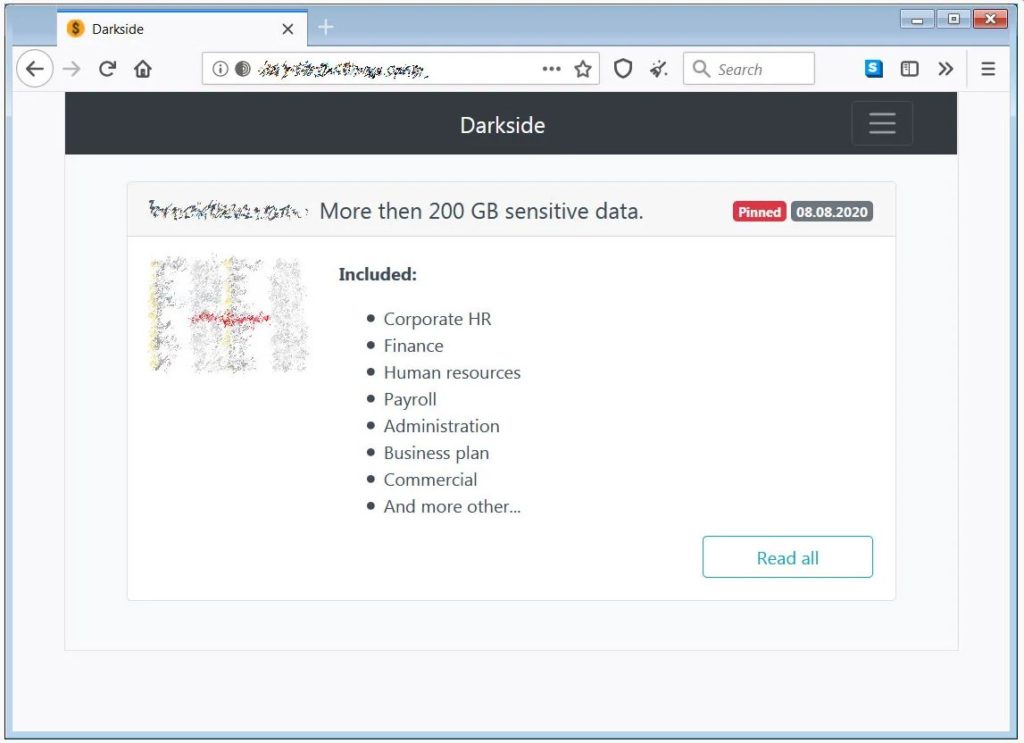
All the stolen data will be published on their website for a time period of six months if the victim does not pay the ransom. This extortion strategy is designed to scare a victim into paying the ransom even if they can recover from backups.
It has been seen that once the victim pays the ransom their stolen data is taken off their website as they had promised to do.
Customized Ransomware Attack
DarkSide will create customized ransomware executable for the specific company they are attacking while performing the attack. The ransomware will execute a PowerShell command that deletes Shadow Volume Copies on the system so that they cannot be used to restore files. In order to prepare the machine for encryption, the ransomware then proceeds to terminate various databases, office applications, and mail clients.
Certain processes are avoided by Darkside while encrypting the computer.
vmcompute.exe
vmms.exe
vmwp.exe
svchost.exe
TeamViewer.exe
explorer.exe
Avoiding an application like Team Viewer is not common and indicates a possibility of the threat actors using the application to gain remote access to computers.
According to a researcher the ransomware utilizes a SALSA20 key to encrypt files. This key is then encrypted with a public RSA-1024 key that is included in the executable.
A custom extension is created using a custom checksum of the MAC address belonging to the victim’s machine.
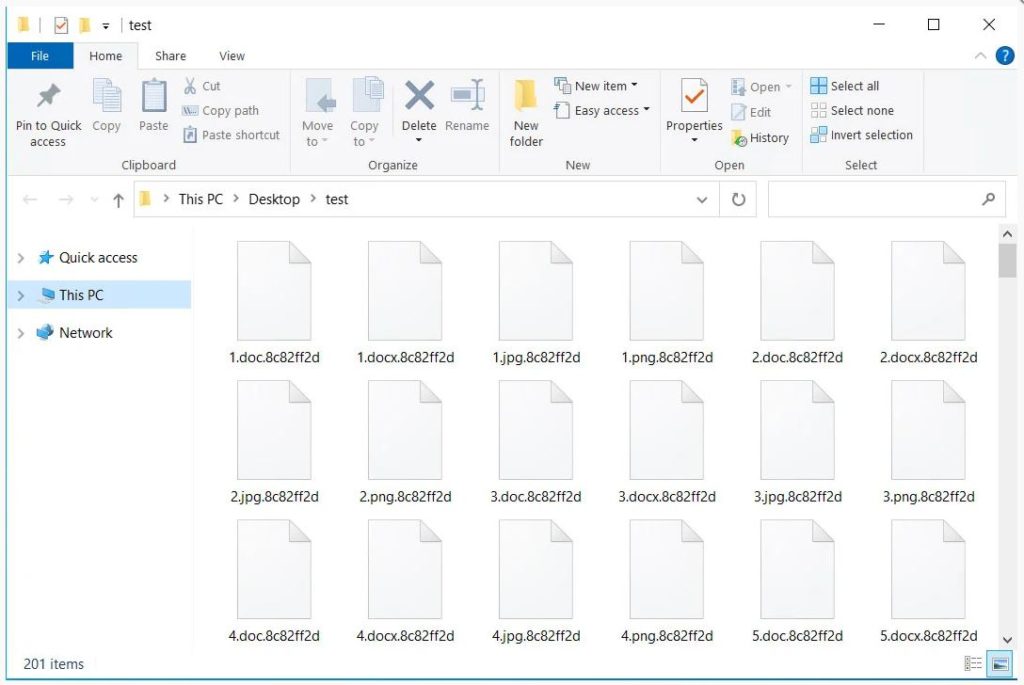
A personalized “Welcome to Dark” ransom note is included within each executable that includes information like the amount of data that was stolen, the type of data, and a link to their data on the data leak site.
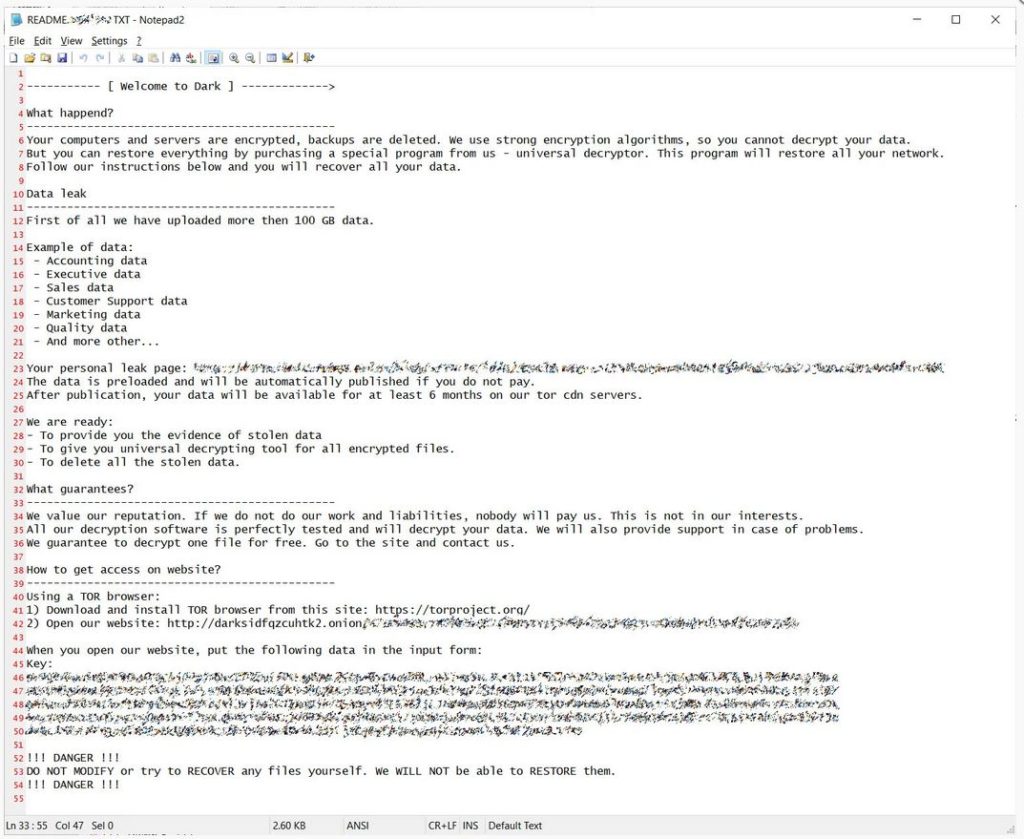
At this moment, the ransomware appears to be secure with no possibility of a recovery that is free of cost.
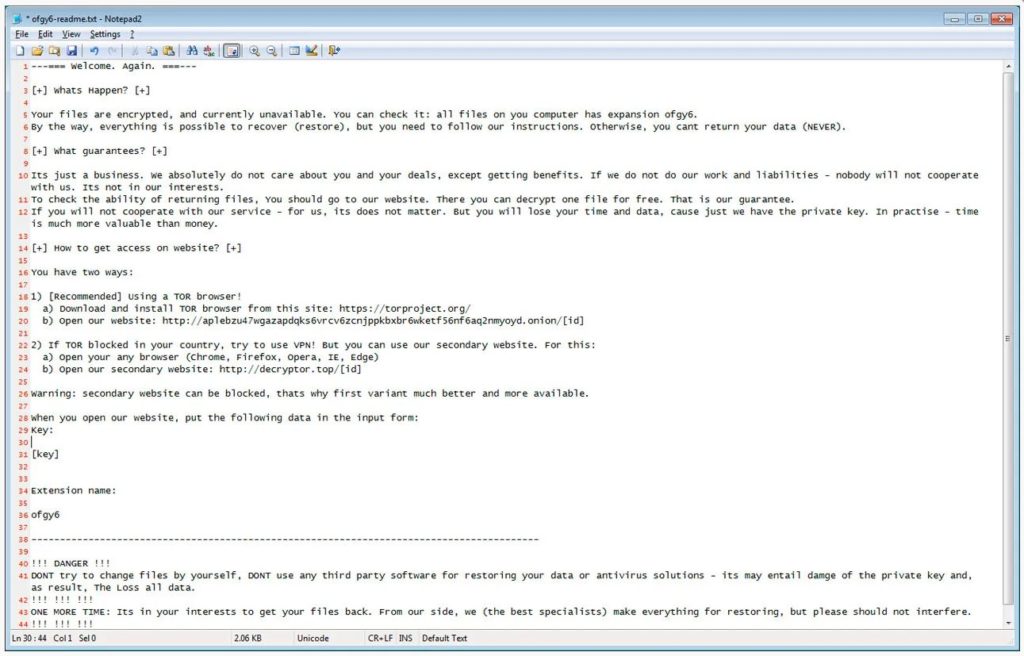
Possibility of being connected to Revil
The Darkside Ransomware has some similarities with the REvil ransomware. The most obvious similarity is the ransom note, which uses almost the same template, as shown in the REvil ransom note below.
During the analysis of Darkside, it was noticed that it would execute an encoded PowerShell script when first executed.
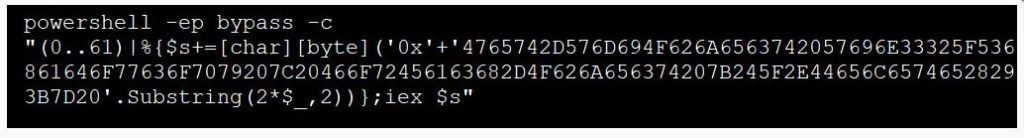
When deobfuscated, we can see that this PowerShell command is used to delete Shadow Volume Copies on the machine before encrypting it.
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();}Using PowerShell to execute the above command is the same method used by REvil.
To read more, please check eScan Blog







